Protecting yourself from Phishing & Ransomware attacks

Best Practices to Protect Yourself from Malware (Ransomware) and Fraudulent attempts on your system
Brian Dye, Symantec’s Senior Vice President, back in 2014 famously said that Antivirus is dead. I don’t want to fully agree with that but as an IT Consultant, I can say that I have seen much less activity on the virus side and much more on the Malware side. Malware is an abbreviation for Malicious Software. The purpose of the software is to gain access to your computer without your knowledge and cause some sort of damage and/or breach.
Does that mean I am ready to remove my antivirus program from my PC? Of course not! There are still enough threats out there to warrant it, not to mention having some old infected file or program get through to my system. But the truth is that many antivirus programs have grown to offer more protection services, including malware protection.
The preferred method of recent attack has been through spam, phishing attacks, malicious websites, and social media capers. By this point, many of you have heard of Ransomware that infects and encrypts your data and then asks for money, in the form of bitcoin to be sent to them to release the decryption info. Without a good backup recovery, this has been so tough to fight that even the FBI’s advice is to pay the ransom! https://securityledger.com/2015/10/fbis-advice-on-cryptolocker-just-pay-the-ransom/
In view of all the deadly computer viruses that have been spreading lately, Weekend Update would like to remind you: when you link up to another computer, you’re linking up to every computer that the computer has ever linked up to. Dennis Miller
Networking computers and then getting them onto the big network called the Internet does create all sorts of problems, but with a little diligence and planning, you can do this and feel safe. These tools and procedures will help you get better protected, but nothing works as well as caution. The internet is the wild west and you have to treat it as such. Rules and regulations of the internet will not do as much as common sense to protect you. Don’t be too trusting and always examine everything and verify, especially where there is sensitive data involved. You do that and you are 90% there and why this is number one on my list.
The Protection Checklist
- Caution and verification
- Anti-virus and Anti-Malware Protection
- Phishing Attacks Protection
- Email Filtering
- Website Filtering
- Backup
- Fake Notice recognition- (Fake Update and Errors in the form of POP Ups)
- Firewalls
- Installation Prevention Solutions
- Passwords Protection
Caution and Verification
I can’t say this enough, nothing works as well as caution. No one should be asking for your login, passwords, account info by email, random phone call, website pop-ups, and such. The only time I share any info is if I call a fully confirmed vendor or if I have actually requested a rest of the password from a trusted website and in some instances if I log in to a trusted site that is authenticating me through preset questions, I know to be authentic. You do that and you will be very well protected and why this is number one on my list.
Anti-virus and Anti-Malware Protection
The first and most obvious is a decent antivirus solution. There are a great many of them in the market (see below link) which will give you more than adequate protection and some even offer built-in firewalls, spam solutions, website security, encrypted passwords storage, web filtering, and more or some combination of these.
Many of these solutions have Anti-Malware protection built into them now, but you can always obtain the independent ones like www.malwarebytes.com, www.superantispyware.com, www.safer-networking.org. Even if you don’t buy the full protection, you can download the free version and manually scan your system. We run full scans once a week and additional quick daily scans daily. Live alerts to our team have been set up in case a threat is detected so that we can respond quickly and potentially knock that PC off the system before it spreads the problem.
To see some signs of malware infection, go to http://tinyurl.com/jc8yb79
Here is a little trick that can help you check my links. Go to http://www.getlinkinfo.com/ and paste in the link from the above line and select “Get Link Info”. This site can tell you if my link is safe. This site is a great tool to check a link you think could be malicious.
Here is a list of some antivirus and antimalware vendors: (http://www.pcmag.com/article2/0,2817,2372364,00.asp)
Phishing Attacks
Phishing is a play on the word fishing. The idea is to catch you and then reel you into a site so that you can input sensitive data, such as your login info, credit card number, or simply install some application without you noticing, then release mayhem on the system. It can even potentially install a key logger (records every keyboard stroke you make to a log file that captures sensitive data without your knowledge as you use your computers, such as your banking website login and password.
The devious attacks have become much more sophisticated and in an age when most of us are way too busy to pay attention to every detail, it is easy to accidentally click on something we shouldn’t or open a malicious email attachment.
Phishing attacks are basically websites that try to duplicate the look of another well-known website such as FedEx, Apple, UPS, Amazon, or such so that they can get you to input your login information and other such sensitive data. They might send you an email saying, please verify this order when you haven’t placed such order or a notice indicating a shipment was delayed, when you are either not waiting for one or coincidentally are awaiting one and log in to the fake website to see what might be holding it up. The trick is to trap you into checking for something that appears to be real and then being malicious.
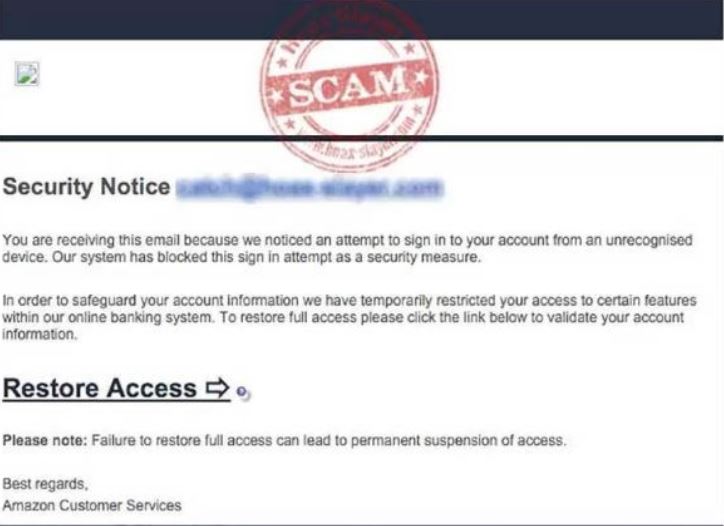
These phishing attacks can come in the form of an email or a website (though I wouldn’t be surprised to see text alerts in the future, tricking the users thinking it’s the App). The image below is a fake email that attempted to fool the users into thinking their Amazon account has been potentially hacked and their confirmation is needed (http://www.hoax-slayer.net/amazon-security-notice-phishing-scam-email/ ). The smart thing to do here would have been to find Amazon’s phone number or support email and contact them directly. Never ever use the emails or links to follow through, even if they are real, always go directly to the customer’s website by typing the correct address (URL) in your browser.
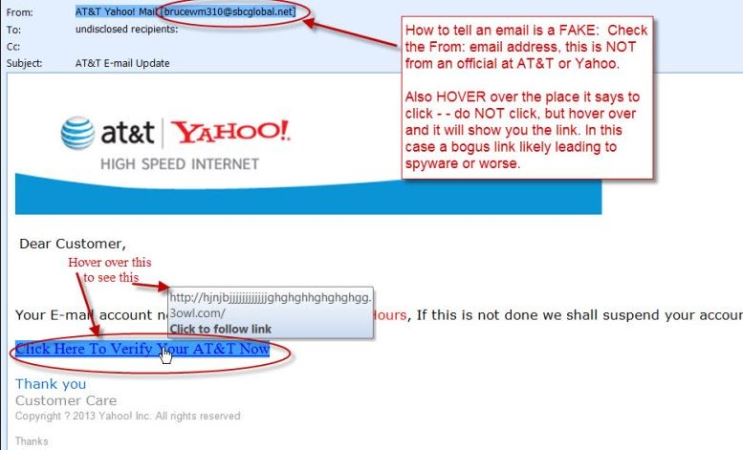
Here is another example that shows you how to determine if it is fake. By hovering over the links in the email, which in the below example is “Click here to verify…” you can see the long weird fake address. If this was from AT&T, that domain would look something like http://www.att.com/…”. Note that it doesn’t have to start with www, it can be, account.att.com, or https://my.account.att.com/login.aspx. But even if it did, I would have not used this email, but logged into the account by going to the real address www.att.com myself.
In the screenshot below, the user was sent to what appears to be a PayPal site but look at the address bar. Even though it looks like PayPal, it’s not really PayPal. In this case, since the computer was updated well with security updates, it noticed it’s a Phishing site and gave the user a warning by indicating “Suspicious Site”. You are not always going to get this, so you need to be cautious and pay attention.
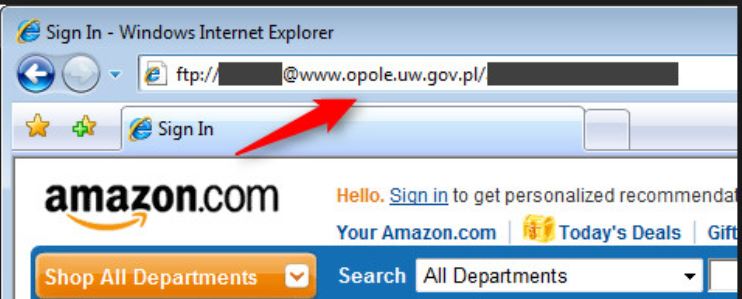
You can also accidentally type the wrong address, such as www.amassson.com instead of www.amazon.com. Believe it or not, these malicious entities actually do research to see what combination of domain names you can accidentally type and get ownership of those domains. Then, they will make that fake site look almost identical to the legitimate one, with logos and such and you wouldn’t have a clue unless you start examining the URL addresses carefully and hover over links. The image below is an example of such a phishing site; the URL, in this case, is not amazon, but the site looks completely like Amazon.
I can hear you now. This is great info, but how do I protect myself against all this? The answer is multi-factored:
- A solid Antivirus/Antimalware solution. I am not a fan of the free versions personally as they remove some features that could be very helpful, especially against phishing.
- Good Antispam Email filtering system to protect against known phishing emails
- Keep your computer up to date as security updates released for operating systems also protect your Internet Explorer program. Keeping your browsers such as Firefox and Chrome up to date is essential in protection these days, though almost all of the later versions keep themselves up to date unless you disable their automatic updates.
- Website Filtering system. There are great solutions out there that will allow you to get further protection against malicious websites by compiling a further list of sites and protecting your system from accessing these sites. Your IT consultant could offer one, especially if your office is on a Managed Service system or you can use services such as www.opendns.com or Barracuda.
- Firewall – Your office should have a capable firewall system that is kept up to date through software updates. They are more expensive, but offer some of the features mentioned above and can help further protect you and keep the costs down. Solutions such as WatchGuard, SonicWall, and Check Point are more than capable.
- Caution – Sorry to say, but one thing the internet is teaching all of us is to lose trust or maybe more positive way of saying it is to use extreme caution. Always VERIFY! But verify through the right resource and channel, not through what suddenly appeared in your email or on the screen.
Backup
If your data is breached with some sort of ransomware that encrypts all your files and then holds them hostage, then you are as good as your backups. You must not only have a great backup solution in place, but you also need to have these backups verified at a set interval too.
There is nothing more important in this business to me than backups because regardless of the damage to a client system, my backups allow me to restore the systems to potentially an hour before the damage. At all our clients, we perform an hourly backup during business hours and keep a two to three-week retention. Some even do monthly retention and keep on a separate backup drive or through their online backup solution.
Although the backup software solutions have come a long way, the old joke for IT people was that backup software must have been written by people who were tortured as children. I am not sure if I greyed faster after the birth of my children or because of dealing with backups. However, thankfully those days are behind us and with imaging software backups that revolutionized the industry, we are in a great age for so many different solutions from locally in-house to online. We have a rule of dual backups at each one of our clients. We actually really do four backups at many.
There are great backup solutions in the market these days and now many of them not only do local backups to a USB Drive connected to your Server or computer, but they will push it online too and have it offsite for a more severe disaster recovery.
Firewalls
Firewalls are obviously the first level of protection for any office, but many still use a simple home router, thinking that is sufficient. Newer firewalls are so full of bells and whistles that they can offer many of the items on the protection checklist. They can block viruses, attachments, prevent users from visiting malicious sites or any specific sites, and much more services. They are also the gateway to your office and must be configured so that they only allow traffic for secured services.
For example, if users are connected to your office through RDP (Remote Desktop Protocol) without a secure VPN (Virtual Private Network) access, then your office is in danger of potential malware that utilizes RDP as this article suggests https://www.hackread.com/windows-remote-desktop-services-ransomware
Fake Notice recognition (Fake Update and Errors in the form of POP Ups)
These are still really phishing attacks. Although I haven’t seen a huge rise in them, I have seen users hit by this. Granted, I see the damage more with home users than office, but still, an important one to point out. In the first image, what looks like a YouTube site is actually some malicious site trying to get you to do some good Samaritan task and dangling a little price. If it sounds too good to be true, then I don’t have to finish the saying! Yes, it is pretty awful the way some people prey on others, but these are pretty awful people who go as far as holding your family pictures hostage for a fee.
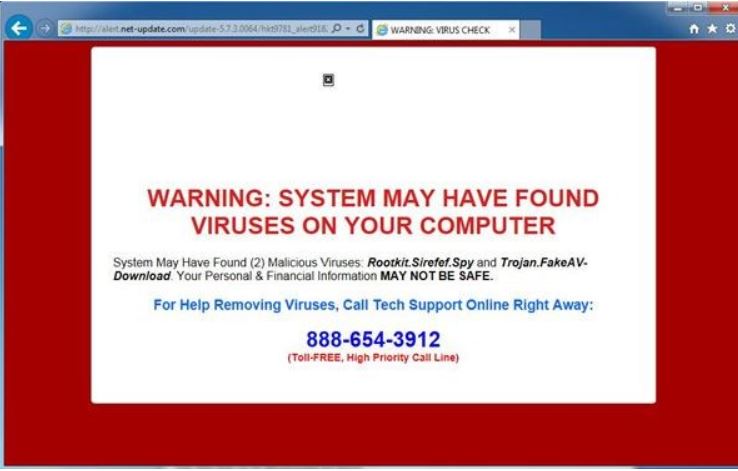
This is the more common one I’ve personally seen. I think by this point you know that we should never trust a number that pops up on your screen. There is a more popular one that actually fakes it as if it is Microsoft. In the case below, I would simply contact your IT guy or close or reboot your computer if you can’t get out of the message. If the message reappears again, then see if you can scan your computer with a good antivirus and anti-malware solution or get professional help. You should also make sure your pop-up blocker is working for your browser. http://kb.mailchimp.com/campaigns/previews-and-tests/enable-pop-ups-in-your-browser though this is not necessarily going to stop it.
Installation Prevention
Ransomware is fast becoming popular installed malware. It can get installed on your computer by exploiting a vulnerability through your computer’s lack of security updates or an email attachment or website download or even clicking on a link on a malicious website. A tech support person at a major antivirus firm even told me that even hovering over a malicious site can install programs, though I haven’t been able to fully verify that.
The one unique behavior we found on ransomware is that it likes to install in the AppData folder on Windows computers. There are a few ways you can protect yourself.
- Anti-Executable by Faronics – http://www.faronics.com/products/anti-executable/ This program basically creates a block and allow a list of what can and cannot get installed on your system. Note that this is a cumbersome procedure and you will need an IT Manager who can implement this solution. Security protection by its nature is tedious, especially when it comes to managing an office network with its own set of complexity.
- Group Policies to prevent applications running from the AppData folder http://www.fatdex.net/php/2014/06/01/disable-exes-from-running-inside-any-user-appdata-directory-gpo/ . This is a bit tricky as some real applications such as Spotify or legitimate Web Applications run from this location and it will block those too. Again, let your IT guy help you with this.
- Bitdefender Labs offer a free utility that gives you protection against certain strains. Not 100% protection, but better than nothing. https://labs.bitdefender.com/2016/03/combination-crypto-ransomware-vaccine-released/ There are other vendors out there that create software just to prevent certain types of Ransomware too, but I haven’t tested them and warn you to have someone professional approve anything that claims to prevent infection before you install it on your system.
Password Changes
Some of the newer versions of Ransomware, such as Bucbi Ransomware (http://www.psgeeks.com/malware/bucbi-ransomware-servers/) are now utilizing ways to crack the passwords. For all system Administrators, it’s a must to have long and super complex passwords, but it is also good practice to change those passwords on a set interval and a lockout policy to disable login after so many wrong attempts.
Passwords should never be saved to your computer on a word or excel document or posted around the office under your keyboard, monitor, or such. Even if the malicious attack doesn’t damage your computer or fool you into paying them a fee, they might steal your documents, then scan them for login/password information.
My advice is to have your passwords saved to a password manager solution such as www.roboform.com or www.lastpass.com. Solutions of this type allow you to keep your passwords in an encrypted location and to access them, you use one master password. Hence, all you have to do is remember one password. This is a great way to create super complex passwords for all the sites you use. For offices that share passwords, there is now even an Enterprise edition.
I will be delving deeply into security in upcoming multipart posts that will delve into securing data and logins.
Conclusion
The landscape of security is a vast one and there are people who dedicate their careers to this field. It is ever-changing and very hard to keep up. These are some of the staples of protection, but even those will alter and change in the coming years. Again, your best defense is caution and common sense, and basic user training on the caution principles, augmented by some or all of these tools.
In my posts, I’ve tried to remove the technical language and make IT accessible for the non-technical. This one might have been a bit more technical, so feel free to contact us if you have any questions or concerns